Get Started
Download AWS CLI and config your profile.
AWS CloudFormation
Setup Linux instance with AWS EC2 and ELB with CloudFormation.
# download the template from Github
wget https://raw.githubusercontent.com/billrain/aws-devops/main/cloudformation/web-ec2-template.yml
# validate template
aws cloudformation validate-template \
--template-body file:///Users/web-ec2-template.yml
# apply template, note the single quote for multi values, must specify at least 2 subnets for multi AZ
aws cloudformation create-stack \
--stack-name ec2-web-stack \
--template-body file:///Users/web-ec2-template.yml \
--parameters ParameterKey=KeyName,ParameterValue=web-ec2 \
'ParameterKey=Subnets,ParameterValue="subnet-f390a285,subnet-cc4c44a8"' \
ParameterKey=VpcId,ParameterValue=vpc-cda7e6a9
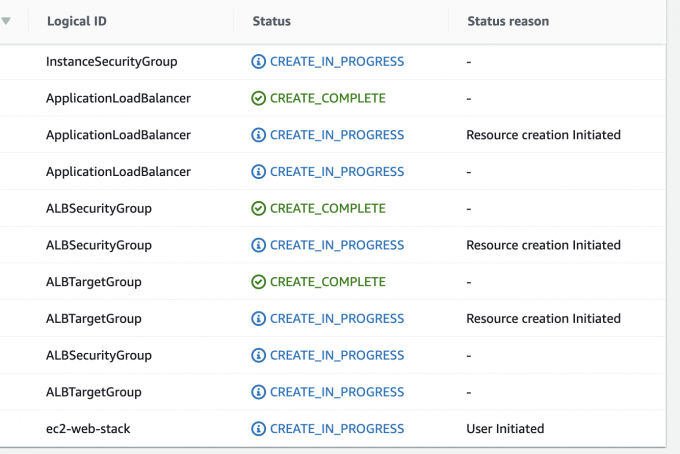
Below AWS resources are deployed by CloudFormation.
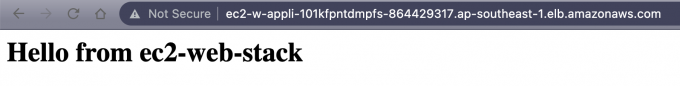
After the stack is ready, open the url offered by ALB, we can see:
CodeDeploy
AWS CloudFormation to create CodeDeploy pipeline
# download the sample app from AWS and save to your local
# create AWS CodeCommit Repo
aws codecommit create-repository --repository-name aws-SampleApp --repository-description "aws sample app"
# from your local app path
git init
git add .
git commit -m "init"
git remote add origin https://git-codecommit.ap-southeast-1.amazonaws.com/v1/repos/aws-SampleApp
git push --set-upstream origin master
# validate template
aws cloudformation validate-template \
--template-body file:///Users/codepipeline-codecommit-events-yaml.yaml
# apply template (requires deployment group)
aws cloudformation create-stack \
--stack-name CodePipe-demo-stack \
--capabilities CAPABILITY_IAM \
--template-body file:///Users/codepipeline-codecommit-events-yaml.yaml
Send CloudWatch log to AWS OpenSearch with Cognito SSO
1. Install CloudWatch agent on EC2 and collect HTTPD/NGINX access/error.log to CW Log Group.
2. Setup OpenSearch domain and config security:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "es:*",
"Resource": "arn:aws:es:YOURS:domain/open-search-pub/*"
}
]
}
3. Subscribe log group to OpenSearch
Lambda function that send log to OpenSearch
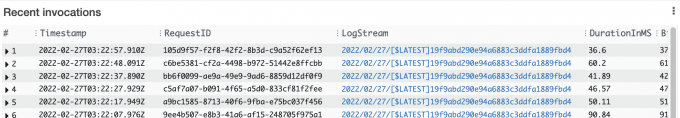
4. Enable OpenSearch
user signon with Cognito.
Create IAM role name: CognitoAccessForAmazonOpenSearch and Cognito_openidentitypoolAuth_Role
Create Cognito User pool: open-userpool
Create Cognito Identity pool: open-identity-pool
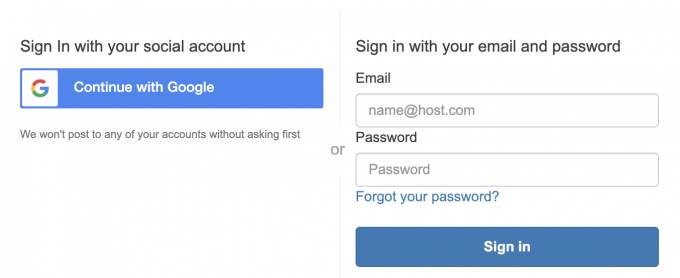
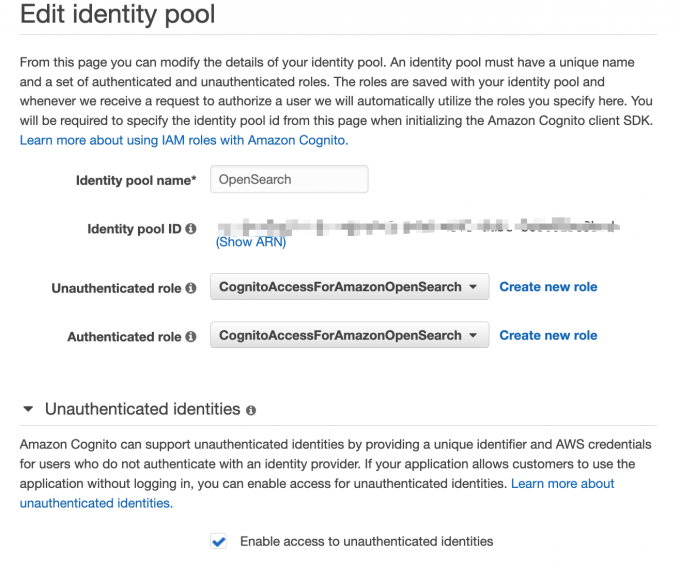 5. Enable Google Single Singon
SSO with Cognito
5. Enable Google Single Singon
SSO with Cognito
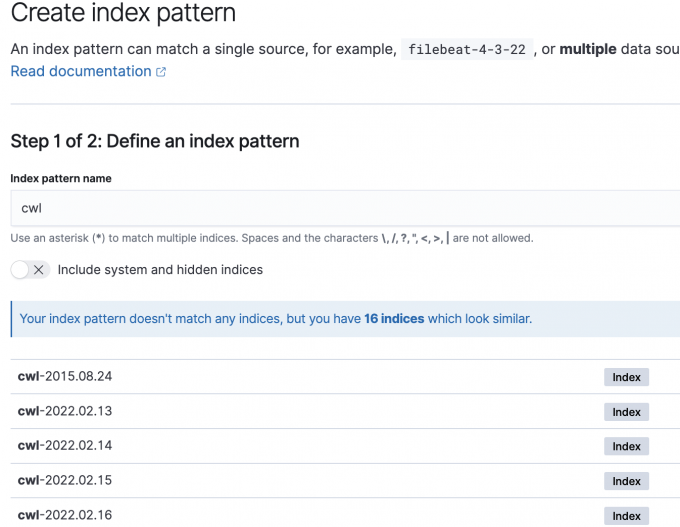
6. Create Index Pattern
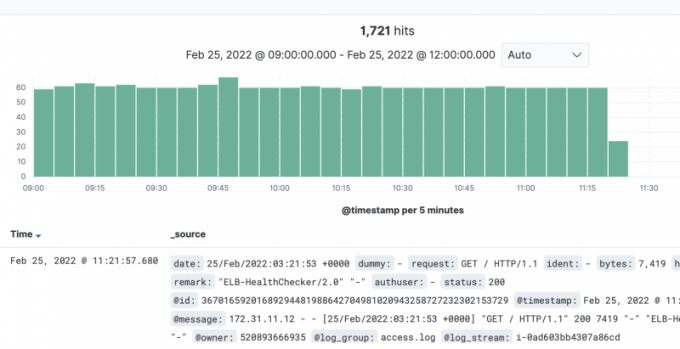
 We can see ELB health check traffic.
We can see ELB health check traffic.